What Is Practical Byzantine Fault Tolerance (PBFT): An Overview
Practical Byzantine Fault Tolerance (PBFT) is a consensus algorithm for distributed systems. It enables systems to reach consensus despite faulty or malicious nodes. PBFT has a leader node called the primary, which proposes a new block of transactions to other nodes. After validating the block, the other nodes send a response to the primary. If a quorum of nodes agrees, the block joins the blockchain.
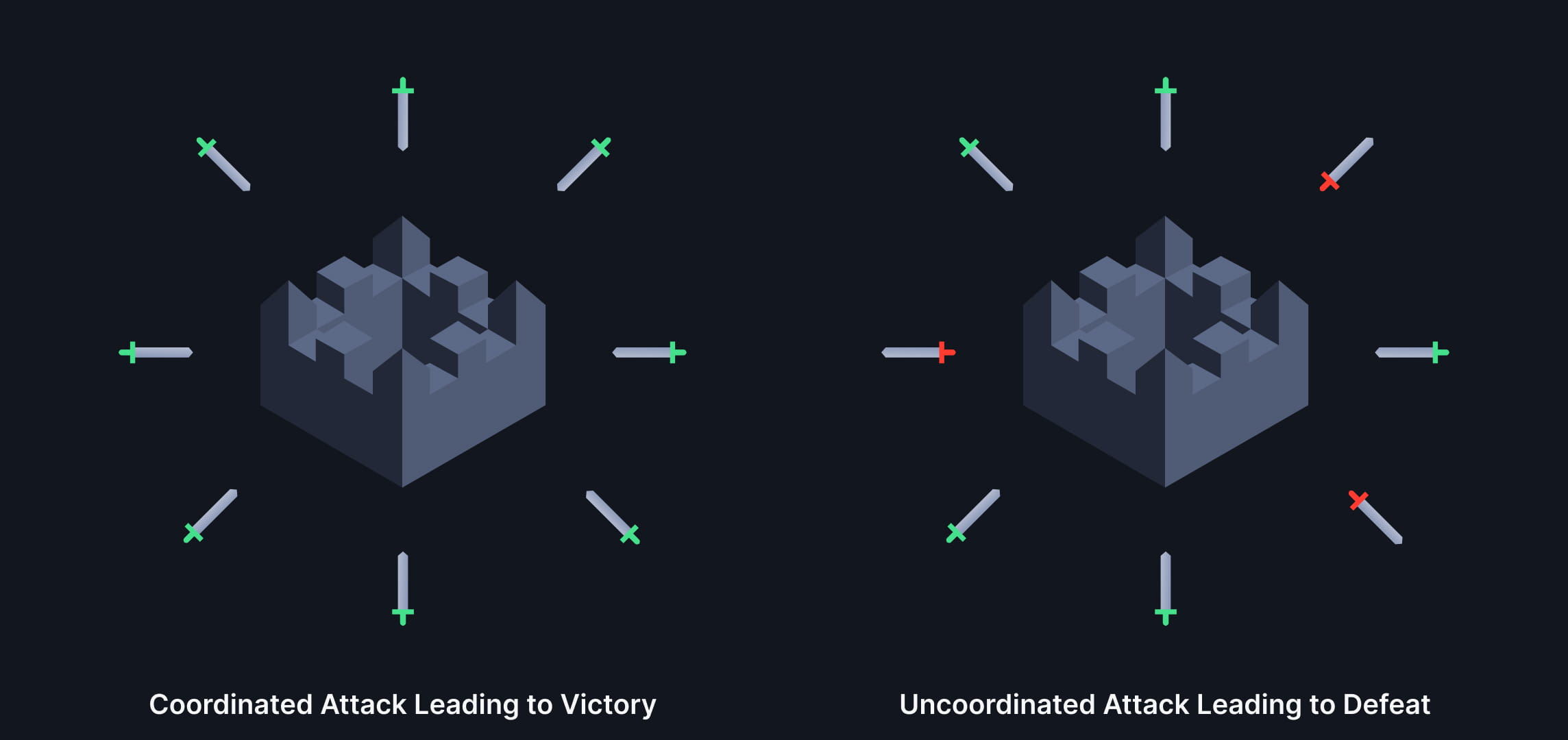
Coordinated attack vs Uncoordinated attack
Practical Byzantine Fault Tolerance Advantages
PBFT excels at handling malicious nodes. Each node has a digital signature, ensuring message authenticity and integrity, preventing tampering and double-spending. Additionally, PBFT achieves consensus quickly without extensive computation or mining, relying on a quorum of nodes.
Handling Malicious Nodes
PBFT uses digital signatures to maintain message authenticity and integrity. It also requires a quorum of nodes to agree on a proposed block before adding it to the blockchain, ensuring no single malicious node influences the consensus process.
Primary Role and Selection in Practical Byzantine Fault Tolerance
The primary node in PBFT proposes a block and broadcasts it to the network. Primary node selection occurs through a round-robin process, with backup primary nodes available in case of failure. This approach ensures a balanced power distribution and prevents single points of failure.
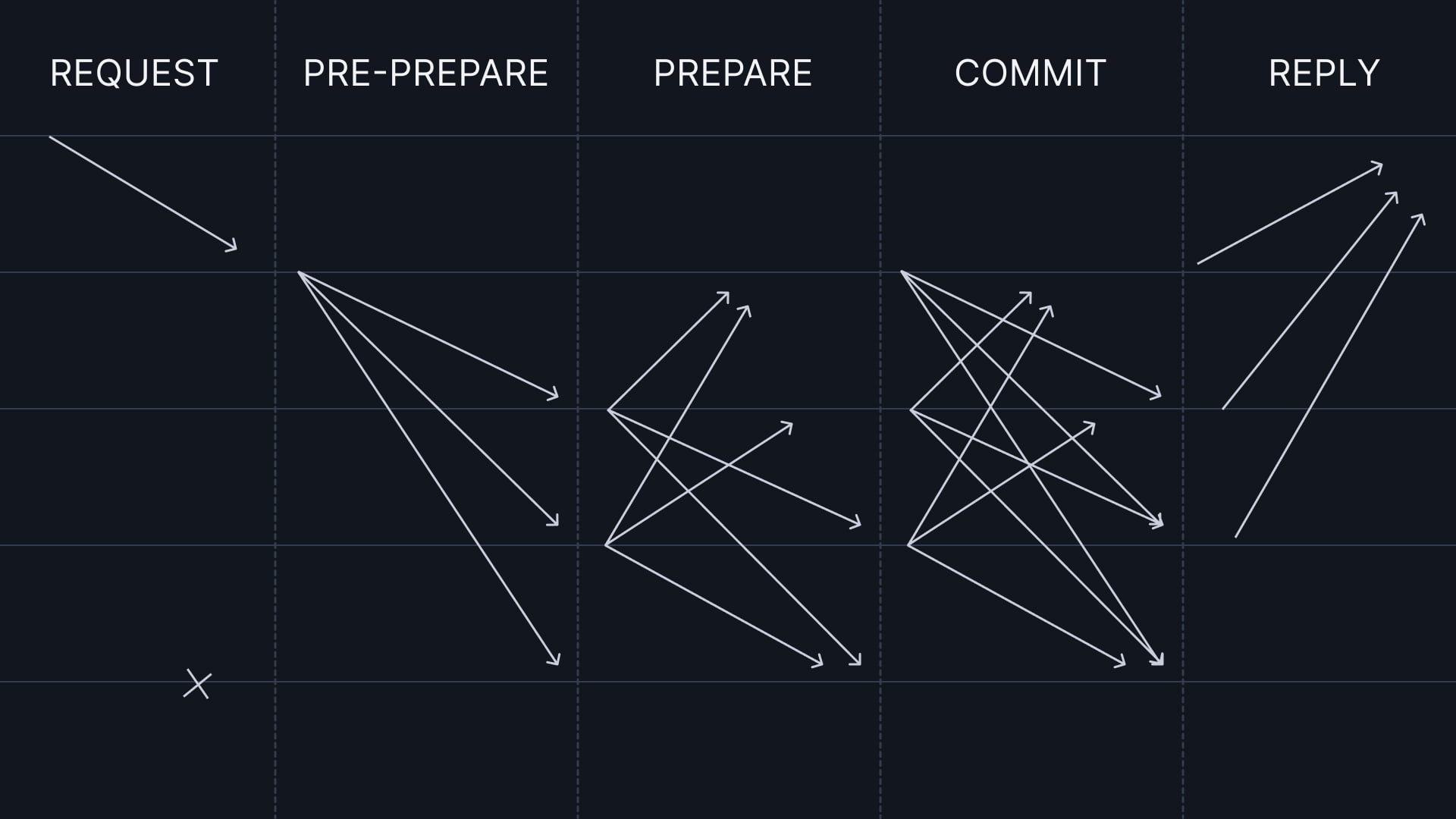
Normal case operation
Security Vulnerabilities and Mitigation
Like any system, Practical Byzantine Fault Tolerance (PBFT) isn’t immune to potential security vulnerabilities. Here are some vulnerabilities that could potentially affect PBFT:
- Sybil attacks: Malicious actors can create multiple identities to control a network during Sybil attacks. In PBFT, this could allow a single entity to control most of the replicas in a network. To lessen this vulnerability, PBFT uses a network topology that limits the number of replicas under a single node’s control.
- Denial-of-Service (DoS) attacks: DoS attacks can make PBFT vulnerable by preventing honest nodes from communicating with each other, causing a failure in the consensus process. To address this vulnerability, PBFT employs a view change mechanism, which enables the network to recover in case of a failure.
- Crypto attacks: PBFT depends on cryptographic functions to secure the network. If a malicious actor manages to break the cryptography, they could potentially compromise the security of the entire network. To address this vulnerability, PBFT employs strong cryptographic algorithms and key management systems.
- Byzantine failures: PBFT can tolerate up to one-third of the network’s Byzantine replicas. However, if more than one-third of the replicas become Byzantine, the consensus process could fail. To address this vulnerability, PBFT assumes that most replicas are honest.
To address these vulnerabilities, PBFT uses various mechanisms, such as network topology, cryptographic algorithms, and view changes. Additionally, researchers continue to conduct studies to further enhance the security of PBFT and other consensus algorithms.
Comparing PBFT with Proof-of-Work and Proof-of-Stake
PBFT differs from other consensus algorithms by being more energy-efficient and equitable. It does not require mining, computation, or reliance on stakeholder wealth or computing power. PBFT is designed for private networks, while Proof-of-Work and Proof-of-Stake are used in public networks.
| Attribute | (PBFT) | (PoW) | (PoS) |
|---|---|---|---|
| Basic Concept |
Voting-based consensus mechanism |
Solving a complex puzzle to validate transactions and create new blocks |
Validators chosen based on the number of tokens they hold or are willing to “stake” |
| Energy Consumption |
Low | High | Low |
| Security | Resistant to Sybil attacks | Secure if the majority of miners are honest |
Relies on the honesty of majority token holders |
| Transaction Speed |
Fast | Slow | Faster than PoW, but varies depending on implementation |
| Centralization Risk |
Can be centralized if nodes are controlled by a few entities |
Decentralized but can face centralization issues due to mining pools |
More decentralized than PoW, but centralization risks exist |
| Incentive Model |
Validators receive transaction fees |
Miners receive block rewards and transaction fees |
Validators receive block rewards and transaction fees |
Real-World PBFT Use Cases
PBFT finds use in blockchain networks, finance, healthcare, and supply chain management. For example, Hyperledger Fabric and JP Morgan’s Quorum blockchain employ PBFT for fast and secure transaction processing.
- Blockchain Networks: Many blockchain networks, including Hyperledger Fabric, use PBFT. Hyperledger Fabric, an enterprise-grade permissioned blockchain, adopts PBFT as its consensus algorithm. PBFT offers fast transaction validation times and ensures network security.
- Finance: Financial institutions also use PBFT to process transactions quickly and securely. For instance, JP Morgan’s Quorum blockchain relies on PBFT to guarantee the security and immutability of transactions.
- Healthcare: PBFT enables the secure sharing of patient data among healthcare providers. For instance, a PBFT-based blockchain network can securely share electronic health records between healthcare providers while maintaining data privacy and security.
- Supply Chain Management: PBFT helps track goods in a supply chain and ensures that all parties involved receive notifications about any changes. For example, a PBFT-based blockchain network can track the origin of a product, its journey through the supply chain, and any modifications made to the product.
