Send protection SoftNote wallet
Tectum proudly announces the addition of send protection to SoftNote wallet transactions. The extra layer of security will discourage malicious third parties from accessing your account.
This article will simplify this feature and outline its benefits to users.
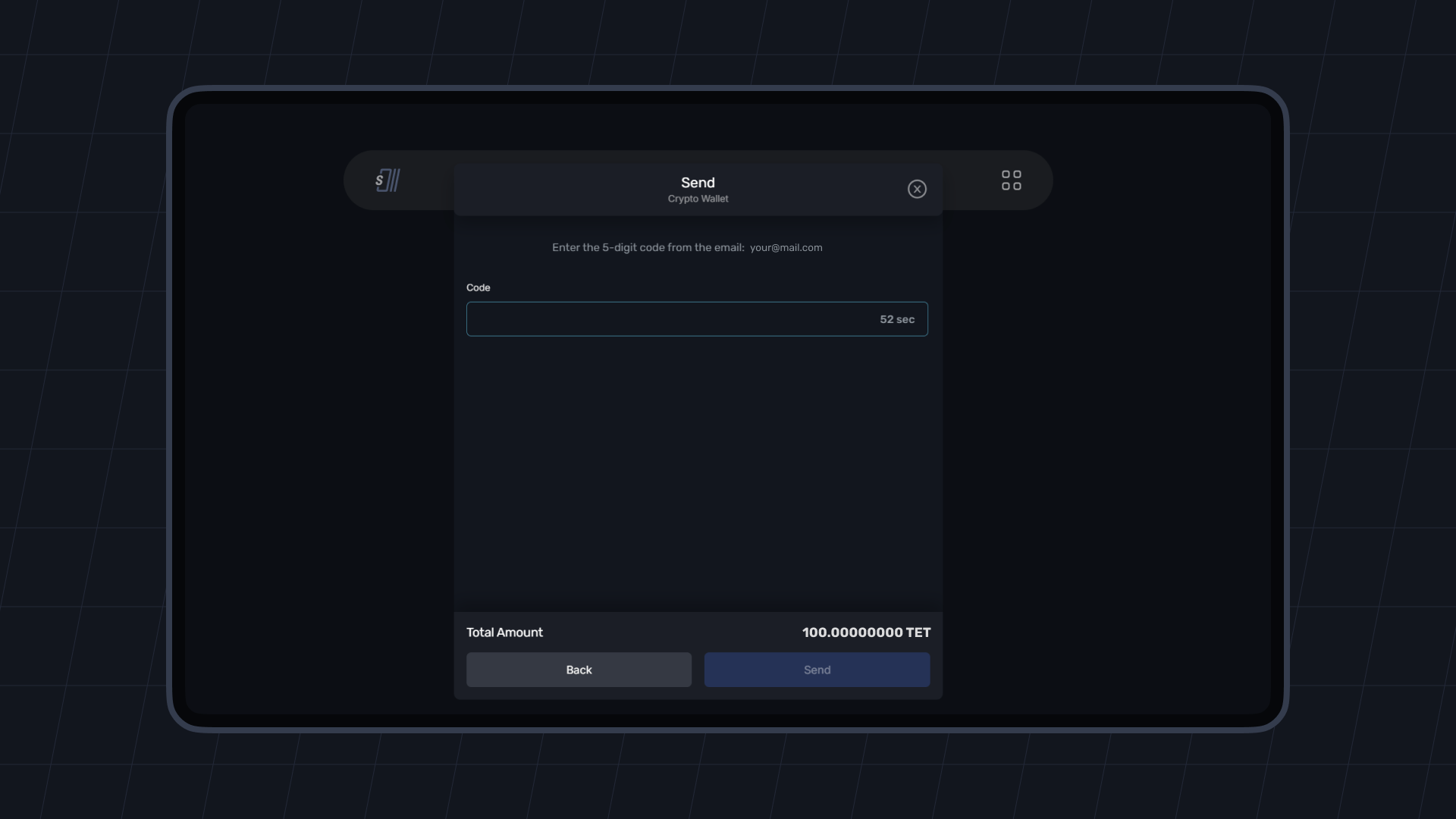
This is a safety measure that demands extra authentication from users after they have initiated a transaction. Let’s imagine you want to send 0.2 BTC.
You must now verify that you, as the account owner, are the one sending those amounts. Upon initiating the transaction request, SoftNote Wallet will request you enter a one-time code sent to your email or from Google Authenticator (2FA)
You must enter that OTP to complete the transactions. Otherwise, the funds will remain in your account.
How Will This New Feature Work?
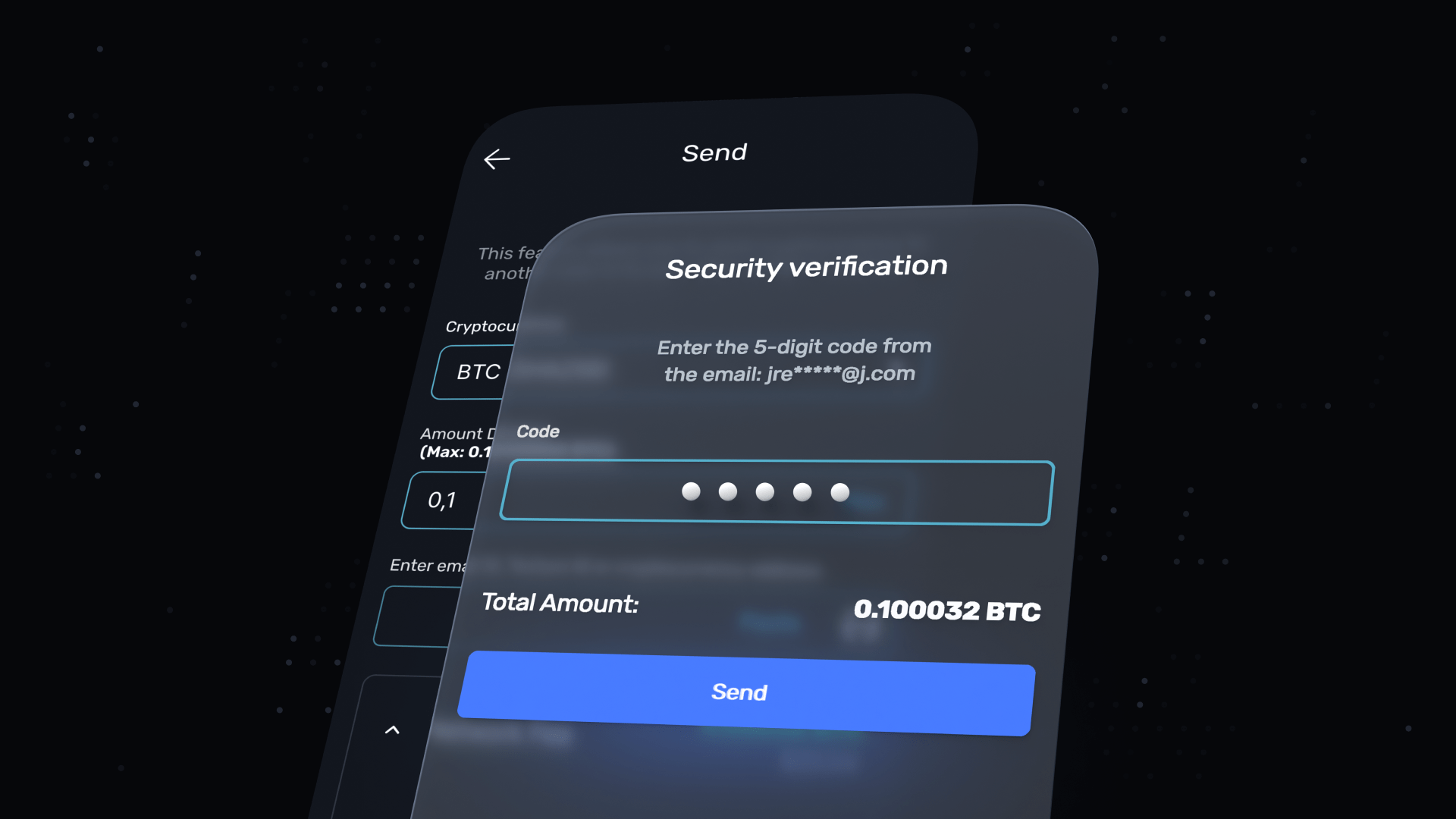
Initially, people only needed one-time passwords to access their accounts. After logging into the account, they can send or receive money without any additional requirements. The is set to further strengthen security.
As shown in the illustration above, the process begins with entering the necessary details for transferring cryptocurrencies. After which, you’ll press “send”. Upon doing so, SoftNote will send an OTP to the email address or Google Authenticator
This time-based code must be used within a specific period, or it will become redundant. Should that happen, you must request another OTP to proceed.
While there are plans to enable users to deactivate this measure, it will remain automatic for the time being.
Benefits of the Send Protection Layer During SoftNote Wallet Transactions
From a glance, offers security as a benefit. However, this is not just textbook protection from cyber threats. In a previous post, we discussed some security risks associated with crypto wallets.
One of those vulnerabilities includes cloned websites that hackers use to steal user information. This process involves creating a lookalike website to fool unsuspecting persons. The clone will have the same interface and a very similar URL to the original website.
This trick works particularly well on those who use Google Search to access the website of wallets. Cybercriminals often sponsor their sham website to appear as a top result. The victim enters his personal information into the fake site, thinking it is the real deal.
Scammers then use his login information to access his actual account and steal his/her tokens. comprehensively puts a stop to this mode of operation, as the hackers must also provide a one-time password sent to the email address linked to the account.
Unless they can access that email, it is impossible to transfer funds from the wallet. This gives you adequate time to change your password and recover your account without losing any money.